Enforce NIST Password Requirements
NIST Password Guideliines (based on SP 800-63B)
The National Institute of Standards and Technology (NIST) is responsible for creating the standards and guidelines to help federal agencies implement the Federal Information Security Management Act (FISMA). NIST guidelines should be cost effective and have the end goal of keeping company information safe.
NIST gives the following recommendations to help guide password management at an enterprise level:
- Password length should be 8 to 64 (or more) characters.
- Turn off password complexity (stop requiring 3 of 4 character types).
- ASCII and Unicode characters should be allowed.
- Password hints should not be used.
- Check for known bad passwords This implies checking against a list of breached passwords and using a dictionary to eliminate common passwords, keyboard patterns, etc.
- Use throttling to limit failed authentication attempts.
- Do not require users to change passwords.
- Discourages the use of SMS for 2nd factor in multifactor systems.
A password filter is recommended to improve compliance and meet NIST password requirements. The previous recommendations can be met using the nFront Password Filter. Many companies trying to reach NIST SP 800-63 compliance have already implemented our software and are NIST compliant.
The New NIST Password Requirements
The new NIST requirements are getting quite a bit of attention.
The new NIST requirement eliminate the need for complexity and periodic password changes in favor of longer passwords/passphrases. The new requirements allow a user to keep the password forever unless a security breach deems that all uses must change passwords.
Here is a summary of the requirements and how nFront Password Filter offers settings to help with the requirements.
- Clearly communicate information on how to create and change memorized secrets.
- Clearly communicate memorized secret requirements.
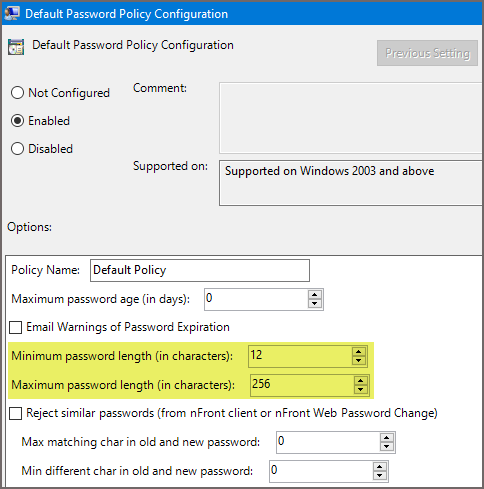
- Allow at least 64 characters in length to support the use of passphrases. Encourage users to make memorized secrets as lengthy as they want, using any characters they like including spaces), thus aiding memorization.
- Do not impose other composition rules (e.g., mixtures of different character types) on memorized secrets.
- Do not require that memorized secrets be changed arbitrarily (e.g., periodically) unless there is a user request or evidence of authenticator compromise.
- Provide clear, meaningful and actionable feedback when chosen passwords are rejected (e.g., when it appears on a “black list” of unacceptable passwords or has been used previously). Advise users that they need to select a different secret because their previous choice was commonly used.
Since users will be rewarded by not having to change their password once they adopt a great “secret” they should take time to make a good choice. Taking a common rote phrase like “to be or not to be” would not be a good choice. Names of books or movies would not be a good choice either. Users should think of a phrase they can easily remember and consider adding a few unique keywords. For example, perhaps a user wants to use the phrase “always eat your vegetables.” Maybe they can use the name of a person or pet to make the phrase more unique. So a new phrase may be “Aunt Mary always says to eat your vegetables.” This is just a suggestion. Exact training will depend on the organization and some will take a more robust approach than others.
With regard to Windows, there is a big difference in passwords that are less than 15 characters and ones that are more than 15 characters. Passwords less than 15 characters are much more at risk because they are stored using a weaker hash format that is easily and quickly cracked using Rainbow tables. Therefore, you want to use a minimum of 15 characters to consider the password a passphrase.
We offer an optional client you can distribute to the Windows workstations. The client can show the exact rules on the screen.
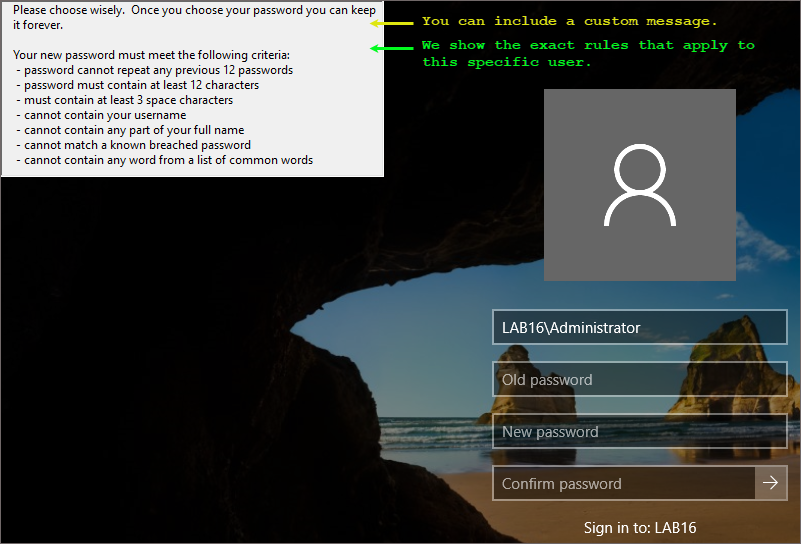
nFront allows you to have passwords lengths from 0 to 256 characters.
nFront also has settings to help promote the use of passphrases. You can require a minimum number of spaces to be used in a new password.

Depending on your use of a dictionary and composition/strategy regarding the dictionary you may need to skip it for longer passwords / passphrases. We can do that too.
If your dictionary contains a lot of common words that would be used in passphrases (like ‘and’, ‘the’, ‘for’, etc.), you will want to skip it for passphrases. However, a better strategy is to use a smaller dictionary that does not contain those common words but does effectively block poor choices. So perhaps use a dictionary with 200 commonly hacked passwords plus your company name, products, brands, office locations, local sports teams, etc. Such a dictionary may only be about 500 words but can be very effective and will not block most passphrase choices.
You can also configure nFront to scan a "breach corpus" of known compromised passwords.

You can turn off Microsoft complexity in the domain password policy.
You can set the Windows domain password policy to allow users to keep passwords for an unlimited amount of time.
This is really saying you need to use a dictionary to black list commonly used words, patterns, etc.
nFront Password Filter can be configured to check a dictionary file. We suggest you put the dictionary file in the netlogon share so it will replicate among your domain controllers. It will be consistent and you can edit the file from any DC if needed. Our default dictionary file comes with 6,000 words, phrases, patterns, etc. We suggest you customize it and include your company name, products, brands, terms from your industry, local sports teams, etc. You can configure the product to check some of the common substitutions like ‘$’ for the letter ‘S’.
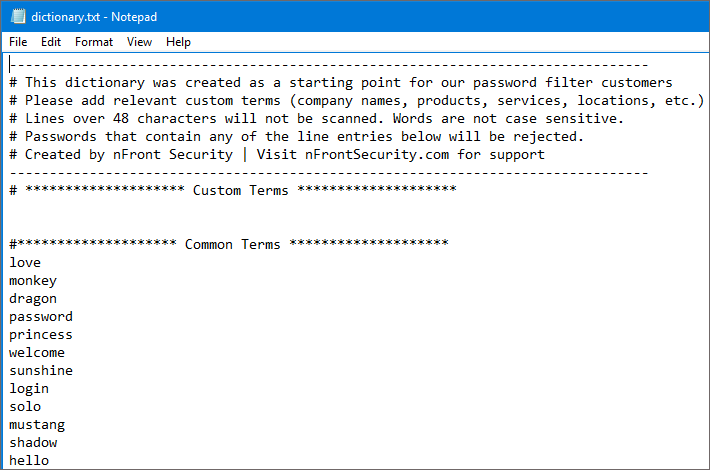
Our client can provide feedback down to the dictionary word(s) on which the password change failed.

